Corelight from PointWire

Threat Hunting
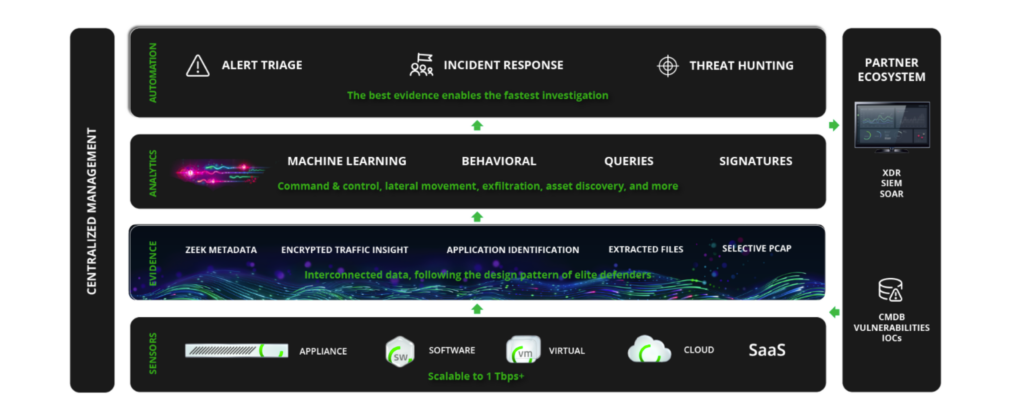
Defenders have always sought the high ground in order to see farther and turn back attacks. Corelight delivers a commanding view of your network so you can outsmart and outlast adversaries. We capture, interpret, and connect the daa that means everything to defenders.
What is Threat Hunting?
At a high level, threat hunting is actively looking for adverseries in your network when you don’t know if they’re inside. This is different from indicator matching, which is only watching for well-known signs of attackers, for example, IP address(es) or file hash.
Usually conducting a thread hunt involves researching a theory, or hunch, and then analysing data looking for something interesting. Items that are interesting can take many shapes.
Why conduct a threat hunt?
Most host-or network-based detection systems rely on matching, otherwise known as signatures, to generate alerts to signal defenders that there is something unwanted in the network. However, attackers are continually evolving to evade detection, and signatures are developed only after the artifact was discovered in another network. So, if you're not hunting for artifacts in your environment, how will you discover that attackers are evading you current defences?
Hunting has several positive outcomes. The first is you might find artifacts of an active intruder that your current defences missed. Whilst some may think this is a tragedy, it can be a huge win, especially if the intruder hasn’t completed their objective(s). In every hunt, there’s always ~something~ to find.
You may discover network or software misconfigurations that pose a threat, either because they degrade a network performance or introduce a vulnerability. Next, the hunt could yield run-of-the-mill infections such as adware, or other dormant malware that aren’t directly targeting your organisation but are still a threat. Lastly, resource abuse and Shadow IT, services that are not officially supported, can introduce risk through degraded network performance or new adversary attack vectors. Every hunt teaches you something new about the network which will aid in your next investigation.


