Nipper Enterprise from PointWire


The mission-critical need for configuration drift assessment at scale
The size and complexity of today’s enterprise architecture means that configurations of network infrastructure, including routers, switches, and firewalls, are changing daily. Any unplanned or unknown changes to these devices make networks vulnerable, which is why configuration drift must be immediately addressed to minimize the organization’s attack surface and limit the scope of breach in the event of an attack. Continuously monitoring network infrastructure for compliance
with trusted security controls and risk management frameworks, ensures drift is identified and addressed, as it occurs – helping to prevent adversarial privilege escalation and lateral movement, and assuring Zero Trust segmentation. This mission-critical requirement demands automation that can continuously and accurately:
» Assess network infrastructure on an enterprise scale,
» Assure network security and compliance posture in real-time, and
» Prioritize remediation by risk to shut-down attack vectors
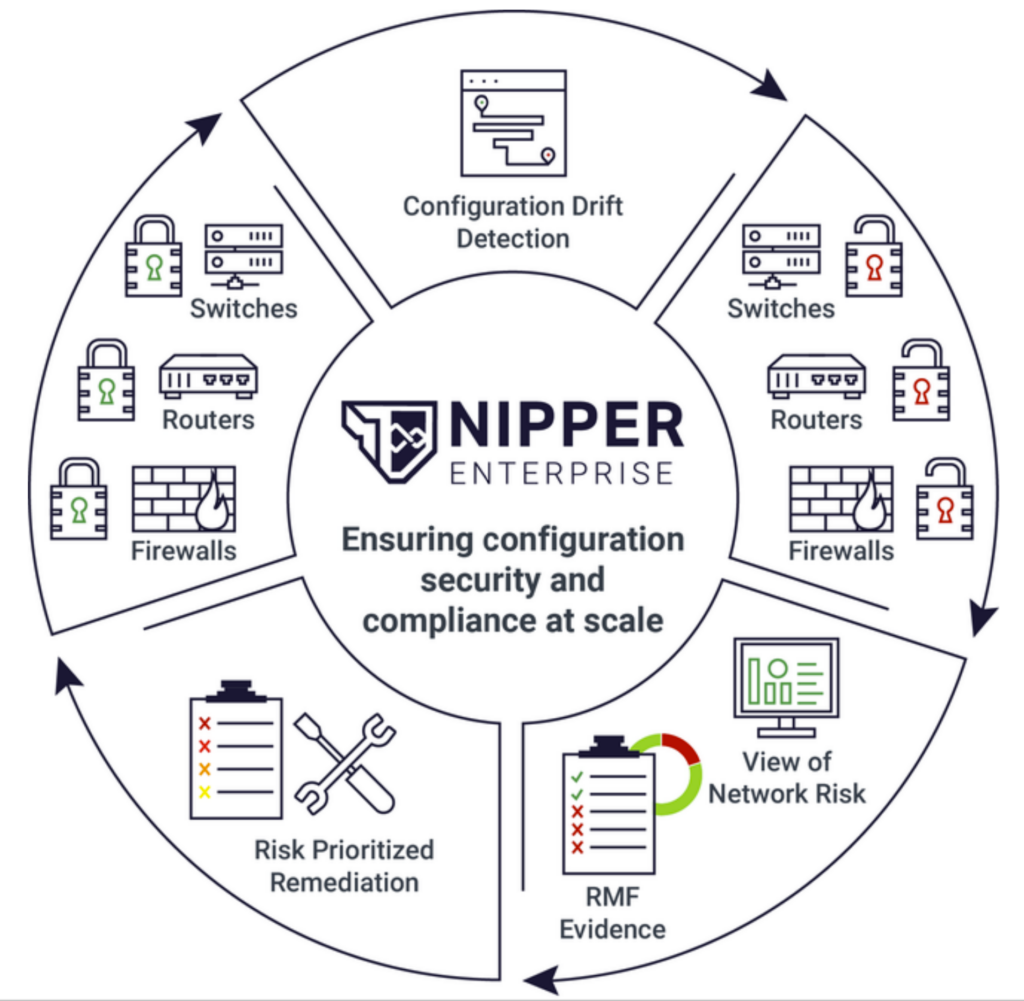
How can Nipper Enterprise help you?
Configuration drift detection
Gain immediate awareness of any device configuration changes, providing assurance that planned network changes have not created new vulnerabilities as well as alerting to unplanned changes.
A comprehensive view of network risk
Prioritizes findings according to network impact if a misconfiguration is exploited, as well as the ease of exploitation and ease of fix.
Evidence for security and compliance assurance
Where security benchmarks or RMF controls are passed/ failed, specific information on the test(s) performed to reach this conclusion is provided, for up to: » 41 (96%) Cisco NDM STIG checks » 55 (60%) Cisco RTR STIG checks » 52 NIST 800-53 controls, across 12 control families via STIG CCIs, NVD and Titania Security Audit » 10 of 11 MITRE ATT&CK “Network” tactics.
Remediation advice to expedite MTTR
Provides device-specific guidance on how to fix misconfigurations, informing POAMs and decreasing remediation time. Provides device-specific guidance on how to fix misconfigurations, informing POAMs and decreasing remediation time.
Introducing Nipper Enterprise
Nipper Enterprise automates the identification of configuration drift in routers, switches and firewalls. Delivering fast, accurate visibility of network configuration posture at scale, Nipper Enterprise is designed to assure network security and compliance in accordance with vendor device hardening best practices and Zero Trust principles.
Nipper Enterprise empowers network owners to:
» Increase coverage and cadence of assessments;
» Evidence continuous compliance assurance for:
» STIGs (CCRI and ZT policy enforcement assurance), and
» NIST 800-53 (DoD RMF and DHS CDM assurance);
» Minimize network infrastructure attack surface via
MITRE ATT&CK misconfiguration prioritization.
Architected for the enterprise
Nipper Enterprise is a horizontally scalable, agentless web-based application. It is designed to support internal and external use cases, via multi-tenanted deployments.
Nipper Enterprise does not require access to devices, but instead connects to a CMDB or Git repository so the application remains stateless and presents a minimal attack surface.
Proactive audits of new or changed configs
New or changed device configurations in the repository, trigger Nipper Enterprise to proactively fetch the latest (changed) configs for assessment.
Inherits config repository segmentation data
Automatically inherits the labels set up in the repository for analysis. Only configuration identifiers are passed to third-party solutions to ensure device locations remain obfuscated, as required.
Flexible deployment options
Nipper Enterprise can be deployed either on-premise with an OVA, enabling deployment in offline environments, or on a virtual private cloud with an AMI.
Customizable audit scheduling by network segment
Schedule audits according to device labels such as network criticality, geographic location, manufacturer, device type, etc
Configurable check parameters
Detailed check descriptions and configurable parameters help ensure network infrastructure assessments reflect organizational policies and risk profile.
Agnostic data pipeline
Risk-prioritized findings are provided in both human-readable and machine-readable formats, enabling integrations with third-party security and compliance tools.
Heard of Nipper before?
You may be wondering what the difference is between Nipper and Nipper Enterprise?
Nipper
Nipper Enterprise
Nipper automates accurate security and compliance assessments of network device configs, providing evidence-based reports and risk and remediation prioritization on-demand.
Nipper Enterprise provides continuous misconfig detection, evidence for continuous compliance assurance and allows users to view vulnerabilities through MITRE ATT&CK lens.


