Vulnerabilities can be a pain, especially when said vulnerabilities are almost 10 years old. A common vulnerability to appear is CVE-2013-3900. Whilst not classified anymore, it’s still quite an annoyance!
So how do I fix it?
To fix this issue, you can do it in a handful of ways, but for this article we’ll focus on two. Luckily for us, Microsoft is aware of this and has changed the way this CVE is handled. Up until July 2014, this CVE was included in security updates, but was later taken out and provided as an opt-in due to the way signature verification was changed with the Windows Authenticode signature format. You can read more about this here: Microsoft Security Advisory 2915720
IMPORTANT NOTE: The .reg file that will be provided is for 64-bit Microsoft Windows machines. If you would like the fix for a 32bit system, the code is available on the link provided above.
Now, we’ll focus on the two different ways to fix this:
Option 1 – Manual Fix
If you only have one machine affected, you can simply double click the .reg file provided below on the affected machine and it will add the registry key values to the machine. You must then restart the machine and the vulnerability will disappear from the machine.
Option 2 – Using Tanium
This is our preferred option. For those utilising Tanium, this is the way we recommend to stamp out this CVE for good. Please be advised, you must have an active Tanium environment to use this option, as well as the Comply module in your environment.
First, you need to identify all the machines with this vulnerability present. Head to Administration > Computer Groups and create a new Computer Group based on the previous tag. Make sure to enable it as a filter and then use the filter bar to type:
Comply - CVE Findings having Comply - CVE Findings:Check ID contains "2013-3900"
This will automatically assign all the computers with the vulnerability into this group. Once saved, you can then head to Administration > Packages and press the New Package button.
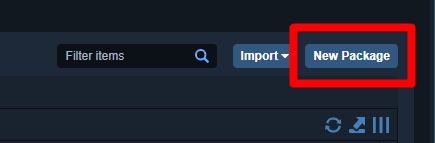
These are the values you need to use for the package:
Package Name: CVE-2013-3900 x64 – Remediation
Command: cmd /c reg import “CVE-2013-3900_X64_Fix.reg” /reg:64
Content Set: Default
After the values are set, add the .reg file, which is accessed using the instructions at the end of this article. Your package should look like this:
Once you’ve created this package, head down to the bottom of the page and save it. You can then check the box next to the package name and press “Deploy Action”
Head down to Computer Groups and select the Computer Group you made earlier.
Press “Show Preview to Continue” to make sure the machines are correct and then deploy the action. This will push the package out to all the machines with this vulnerability. It’s up to you if you wish for this to be deployed on a schedule or just as a one time deployment. Scheduling this action means that any new machines who appear with this vulnerability will automatically get it “patched” once the package is sent out again.
Once your compliance scans have run, you will see the number of machines with this vulnerability decreasing.
And that’s it!
There you have it! That’s the way we were able to stamp out this vulnerability for good.
Fixing these annoying CVE’s like this doesn’t have to be a painful experience. Talk to one of our experts to discuss what options we have available to decrease the pain!
To access the relevant files, please email support@pointwire.co.uk with the subject line of CVE 2013-3900 – Files. Please include your name, the company you work and if you currently have a Tanium environment and we’ll be in touch!


